What is DDoS attack?
A DDoS attack is when a website or online service gets flooded with too many requests from many computers at once. It’s like a traffic jam on a highway, stopping real users from getting through. This overload can make the website slow or even knock it offline completely. Attackers often use botnets—networks of compromised devices—to launch these attacks, disrupting business operations and causing downtime.
A complete solution to protect your business from all types of DDoS attacks
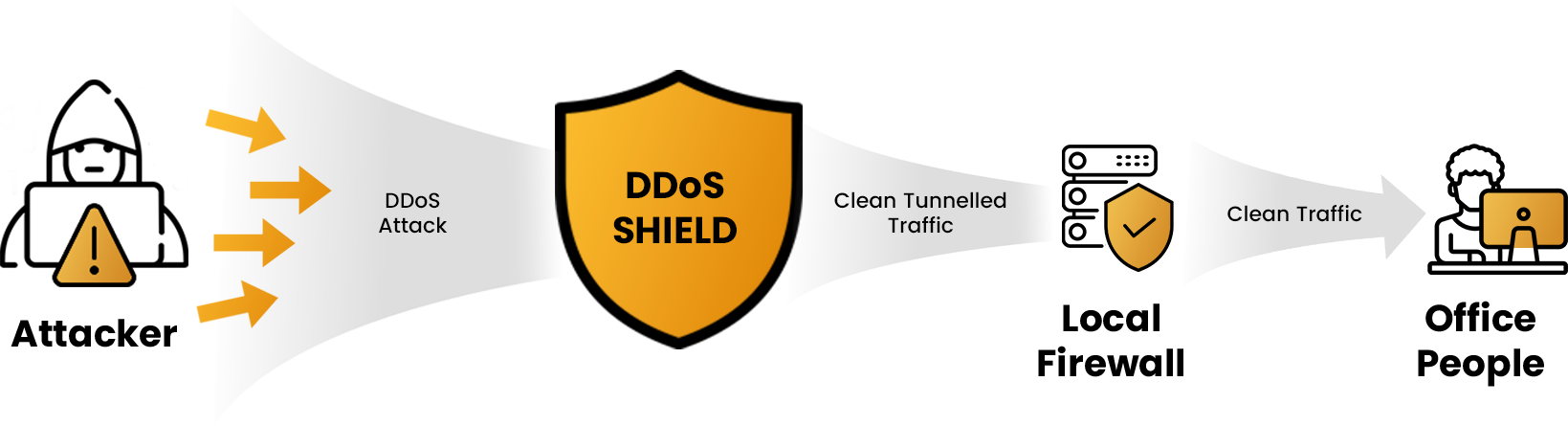
Protect Against Increasing DDoS attacks
Automated defence
Automatically detect and neutralise threats before they affect critical services.
Modular design
Subscription based service that allows addition of different levels of protection as and when required.
Analytics
Access to a web portal for service and status reporting.
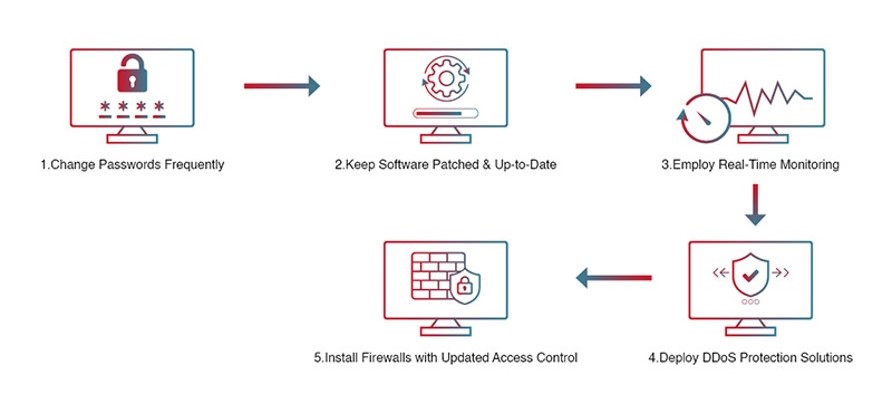
Best Practices for DDoS Protection
Identify Normal Traffic Patterns
Understanding your network's typical traffic patterns helps you identify spikes, anomalies, and unusual behaviour linked to DDoS attacks.
Identify Critical Systems
Organisations should identify critical infrastructure and applications that require protection during a DDoS attack.
Increase Network Bandwidth
Provisioning extra bandwidth can help deal with the traffic spikes associated with DDoS attacks.
Secure Your Network
Do not underestimate the importance of basic network security measures. They can help your organisation establish a robust security foundation and mitigate the impact of attacks.
Our Security Partners
Get in touch
Arrange a call with our team to find out more, get a quote and tailor a solution to your needs.

Frequently Asked Questions
DDoS attacks are frequent and growing, with millions happening yearly. On top of this, the level of sophistication has also increased, making them longer lasting.
Most businesses face them, making strong protection essential across all industries and sizes.
- Volumetric Attacks: A volumetric DDoS attack overwhelms server or network bandwidth, causing slowdown or complete service failure.
- Application Layer Attacks: Application layer attacks target the OSI model’s top layer, aiming at web applications and user-facing services. Application layer attacks mimic real users to exploit app vulnerabilities, disrupt services, steal data, or gain unauthorised system access.
It can last from minutes to days depending on the hacker’s strategy, your company’s defences and its mitigation plan.
We offer DDoS mitigation services targeting volumetric and application attack types, reducing their risks and impacts.







